Aurora Blog

What is Data Breach? How Can CASB Help?
A data breach is unauthorized access, use, disclosure, or destruction of confidential information. In simpler terms, it’s when someone gets your data or enters a

Understanding Attack Vectors and Best Practices to Prevent an Attack
An attack vector is a path or means by which an attacker can gain access to a computer system or network. Enabling them to steal
CISA’s Zero Trust Maturity Model – A Framework for Transitioning to Zero Trust
Significant cyber attacks in 2021, like Colonial Pipeline and JBS Meats, and a continued increase of cyber attacks in 2022 has prompted the U.S. federal

The Importance of Implementing a Zero Trust Security Model
In 2021 there were 1,862 data breaches, according to the Identity Theft Resource Center’s 2021 Data Breach Report, and the number of cyberattacks continue to

Explaining the Cybersecurity Alphabet Soup
To meet the increasing cybersecurity demands today, many organizations are looking for easier ways to meet multiple frameworks such as NIST 800-171, CMMC 2.0, HIPAA,

A Reminder for Regular Vulnerability Scanning
In the wake of Apache’s Log4j vulnerability in December, several cybersecurity vendors announced free vulnerability scanning services. Vulnerability scanning can help businesses identify vulnerabilities within

Addressing the Cybersecurity Burnout Effect
What is the Cybersecurity Burnout Effect? A recent study by 1Password illuminated a trend that may already seem apparent within your organization: there is a

2022 Cybersecurity Predictions By Aurora President, Philip de Souza
Another year at Aurora in the books! In 2021 we made some big leaps. During the first quarter, we joined the Plurilock Family in Plurilock’s

Resources for Log4j Vulnerability
If you are not already aware, on December 9, 2021, a zero-day vulnerability on Apache Log4j, nicknamed “Log4Shell” was reported. It has been characterized as

EDR, XDR, and MDR: Improve Your Detection & Response
Going Beyond EDR You probably are already familiar with Endpoint Detection & Response (EDR). It is a valuable solution for detecting and responding to threats

The ABCs of Cybersecurity
With the fear of being the next victim of a cybersecurity breach, organizations may be tempted to purchase any “next best thing” solution before first

How to Implement Zero Trust?
Zero Trust is a cybersecurity framework that aims to eliminate trust from an organization’s network to help prevent attacks. Zero trust was first introduced in
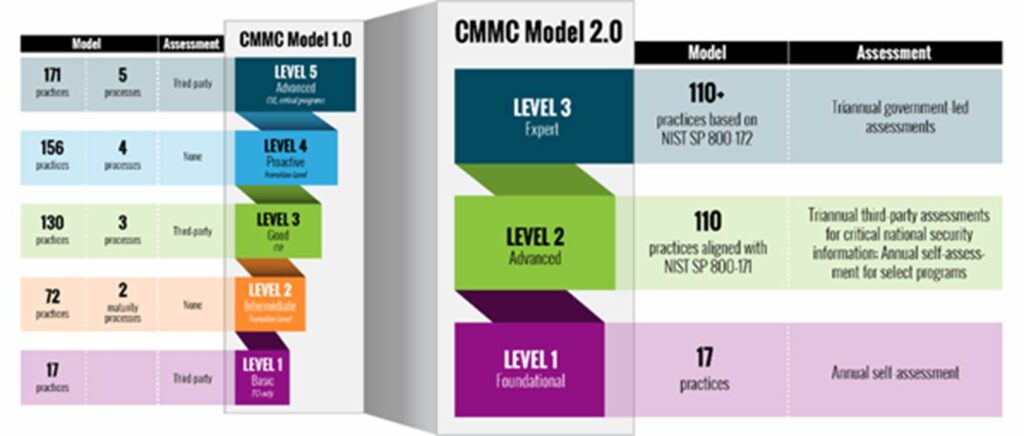
The Launch of CMMC 2.0
The Pentagon recently announced a new version of the Cybersecurity Maturity Model Certification (CMMC) requirements. CMMC 1.0 was announced in 2020 and CMMC 2.0 indicates

Honoring and Thanking Cybersecurity Teams
Holding cybersecurity as a focus of our business, it is important for us to appreciate all of the security teams that we work with to

Making Cybersecurity a Priority
Cybersecurity should be your first consideration when conducting business and navigating the web. As your business constantly adopts new technologies and policies to adapt to

It’s Clean Your Virtual Desktop Day: Why You Should Celebrate
Every year on the third Monday in October, “Clean Your Virtual Desktop Day” is celebrated. Just like how our physical desktops need to be cleaned

