Aurora Blog

Unveiling the Role of Digital Forensics in Cybersecurity
Digital forensic experts often cite the case of Dennis Rader, the infamous killer, who came undone thanks to a forensic investigation. Often referred to as

The Growing Threat of Mobile Malware
Though it was relatively harmless in terms of the devastation that its modern cousins can wreak, the Cabir worm is regarded as the forerunner of

The Danger of Encrypting Viruses in Modern Cybersecurity
Introduction In the Deep Space Nine episode of the hit sci-fi series Star Trek, a virus known as Cascade completely wipes out computer data on

How Failure of Cybersecurity Tools Are Impacting Business Operations
Introduction In the late forties when American aerospace engineer Edward Murphy suffered the mortification of witnessing a mishap in his rocket sled tests, he unwittingly
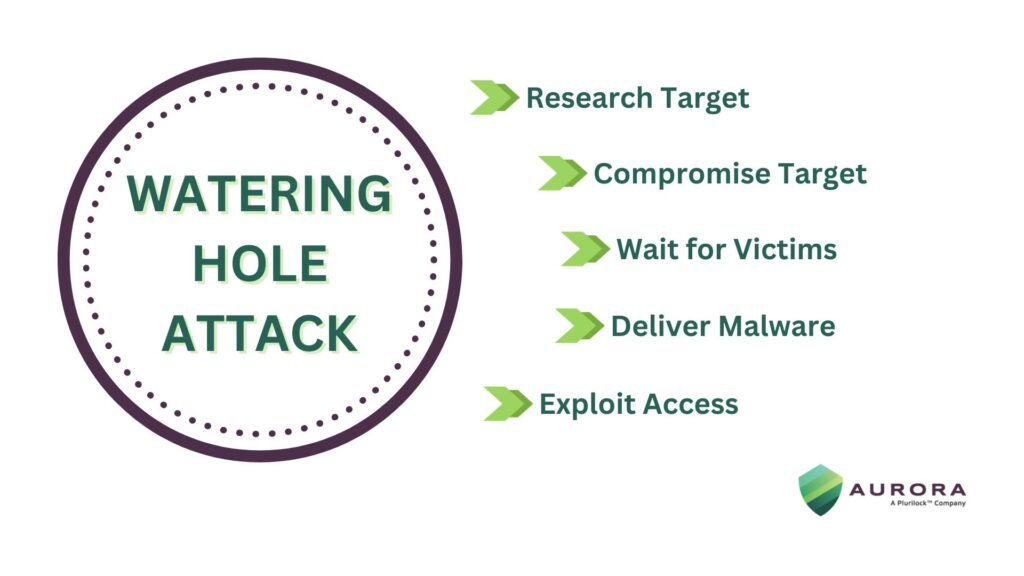
Defending Against Watering Hole Attacks in Today’s Cyber Landscape
Introduction The Chernobyl disaster in 1986, one of the most catastrophic nuclear accidents in history, remains a powerful reminder of the devastating consequences of a

Soft Skills Transforming Cybersecurity Professionals
Introduction From the way ‘soft skills’ has taken center stage in many professions, you’d think it is a concept that is only around a decade

The Importance of Managing Non-Human Identities in Modern Cybersecurity
Introduction Half a century ago, no one would have imagined how times would change in the world of computers. Once believed that computers were the

How Compliance Automation Can Revolutionize Organizational Efficiency
Introduction Amongst the most talked-about requirements of an organization, is the need to be compliant. Every mature industry now calls for organizations within its folds
Understanding Chatbots: Opportunities and Challenges
A decade ago, no one would have dreamed that commercial and other organizations would use a virtual assistant to answer queries which until then were

Open Source Software in a Cyber-Conscious World
Open Source Software in a Cyber-conscious World The March 2017 breach (1) of credit giant Equifax that resulted in the loss of an estimated 143

Building a Global Cybersecurity Plan – Why Collaboration is Key
Needed : A global plan for cybersecurity The story of notorious French drug dealer Charles Sobhraj will go down as one of the biggest manhunts

A Roadmap for Bridging the Gap Between the Demand and Supply of Cybersecurity Talent
Introduction The relationship between demand and supply and their price sensitivity, made famous by early thinkers and economists like Adam Smith and Alfred Marshall, among

Cybersecurity and the C-Suite: A Symbiotic Relationship
The 2019 cyber incident which witnessed Chris Hylen stepping down as CEO of the California-based cybersecurity software services company Imperva, following a massive hack of

How Red Teaming Can Help Organizations
In the world of professional sports, Opposition Analysis – the scientific study of an opponent’s strengths and weaknesses – is widely followed. Professional coaches and

How Threat Hunting in the Cloud Can Help Organizations
High up on mountains in four locations – two in Hawaii and one each in Chile and South Africa – the world’s most advanced space

The Convergence of AI and Social Engineering
Introduction Elon Musk’s recently released AI-generated deepfake video (1) on social networking platform X featuring world leaders attired in futuristic outfits has drawn attention in

