Do You Have All the Components within the SASE Framework?

Security-conscious IT managers are increasingly adopting the Secure Access Service Edge (SASE) framework within their existing cybersecurity policy. The Secure Access Service framework helps to modernize networks and security to meet the evolving demands of your business. SASE provides unified security across users and provides visibility and control. This unified security and visibility are critical […]
It’s A Great Time to Be a Hacker

In the past few months, high profile cyberattacks have been affecting oil, government agencies, and the meat industry, to name a few. Hackers are getting more sophisticated and are finding new successes stealing sensitive data. If IT managers can learn anything from these recent cyberattacks, it is to evaluate your own cybersecurity infrastructure and address […]
Detect Compromised Sessions in Real Time

Most traditional authentication happens once, maybe twice per day. It’s when you first get started in the morning, you sit down, you type in a login password, and then by and large, there’s not any additional checks throughout the day. With Plurilock’s patented technology, we’re checking two hundred and fifty to three hundred times per […]
Who’s on First? Keeping Track of the Mergers & Acquisitions of 2021 So Far

We are six months into 2021 and there has been a lot of movement in the cybersecurity industry as far as mergers and acquisitions go. In fact, Aurora was acquired by Plurilock in April, giving us a wider reach and new innovative solutions to offer our customers. Here’s a summary of some key mergers and […]
How The Recent White House Executive Oder Impacts Your Organization’s Cybersecurity

On May 12, 2021, The US President issued an “Executive Order on Improving the Nation’s Cybersecurity.” This announcement came soon after the Colonial Pipeline Cybersecurity Attack. The cyber-attack exposed weaknesses that exist in the federal cybersecurity infrastructure. Even after paying over 5 million dollars in ransom to recover the data, the pipeline’s temporary shutdown had […]
What is Behavioral Biometrics?

Security practices of the past and present are becoming increasingly ineffective in protecting data as attackers are getting more sophisticated. New technologies are now required to better protect your organization and your customers. Behavioral biometrics is a leading technology aimed at addressing these weaknesses. Traditional Biometric Authentication Traditional biometric authentication would include fingerprint readers and […]
If You’re Reading This, Change Your Password

Is your password still your dog’s name followed by an exclamation point? If so, it’s time to change your password. Far too many people, including employees handling your company’s data, are using weak passwords. The First Thursday of May is also known as World Password Day. In honor of World Password Day, here are some […]
Navigating IAM in the Cloud

75% of all cloud security breaches are a result of poor permission management according to Gartner. As your organization continues to work in the cloud, ensuring that you have the right identity access management tools are essential to best protect your organization. Identity access management (IAM) helps to grant access to the right assets for […]
Addressing Shadow IT

How many third-party Software as a Service (SaaS) applications do you use during the workday? Does your IT department know about all of them? This could introduce Shadow IT into your organization’s environment. The prevalence of Shadow IT has grown increasingly prevalent in the past year as more employees work from home and utilize SaaS […]
Meet Multiple Security Frameworks on One Platform
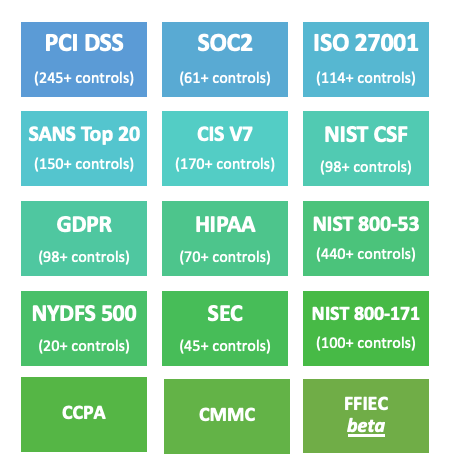
As your organization matures, you may need to meet additional security requirements. For example, many organizations that were previously required to comply with the NIST frameworks now must additionally comply with CMMC. Whatever compliance standards apply to your organization, Aurora can help you harmonize these existing frameworks and apply them to the additional frameworks. At […]
