Professional Services
The goal of Aurora Systems Consulting, Inc is to address the information security requirements of national and international clients. With a comprehensive suite of consulting and managed security services that are practical, efficient and cost effective, we can become the trusted advisor for any client.
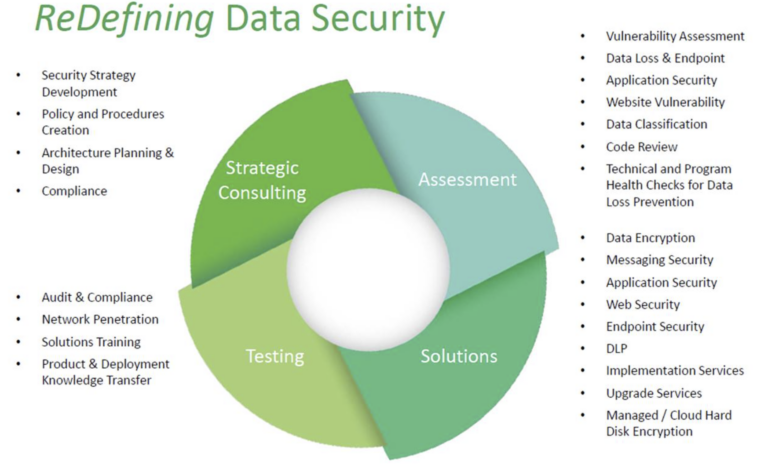
Our team has delivered numerous assessments for small and large companies in just about all lines of business from financial and medical, to manufacturing and high technology, to retail and food service industries. The consulting model and managed service lets us be your partner in your ongoing struggle for security in an insecure world while remaining extremely price competitive.
During all engagements, we work closely with the client’s staff, sharing information and educating the staff when possible. We want to partner with our clients rather than be a point solution provider. Security is a long process that cannot be solved by any one engagement. The results of all engagements are tailored to the client’s requests, needs and business goals, with constant communication every step of the way, and we can speak to any level of the organization from CEO and CFO to technicians and sales staff.
Aurora provides our customers with a strategic approach to data encryption. From performing a data and systems audit for compliance, to consulting, implementation and training. Aurora helps our customers understand their vulnerabilities by performing a data inventory audit. We then consult with them and help them plan a central platform-enabled approach to data encryption. This often includes project planning, deployment services and knowledge transfer and documentation.
Lost laptops containing unencrypted data have become an almost routine way for enterprises of all sizes to lose sensitive data. Since 2009, Aurora® offers full disk encryption on a software-as-a-service (SaaS) subscription. This includes Symantec Universal Server and Symantec’s Windows®, Mac OS®, Red Hat® & Ubuntu® Whole Disk Encryption software on a month-by-month “pay as you grow” basis.
Symantec Whole Disk Encryption locks down the entire contents of a server, laptop, desktop, external drive, or USB flash drive, including boot sectors, system files and temp files. The encryption is transparent to the user, automatically protecting data. The service includes the centrally managed Universal key server, pre-boot encryption software, a key recovery service, and comprehensive reporting on the encryption status of each machine for compliance and auditing. Laptops or desktops running the software can only be accessed by providing a passphrase or key, which means that should they be lost or stolen, all hard drive data remains encrypted and inaccessible.
Aurora implements solutions to help our customers deal with the ever increasing vulnerabilities and targeted attacks through email. We have partnered with vendors that build solutions and industry-leading global reputation systems to track and block emails with malicious content. Our Anti-spam, Anti-virus and Data Leakage solutions have received multiple industry awards for blocking malicious content and for preventing the leakage of company information assets via email, keeping email servers and employees safe from dangerous emails, while preventing data thieves from stealing employee and customer information by spoofing email accounts and phishing attacks.
Aurora provides security audits and application vulnerability assessment services. We help our customers secure their web-facing servers by implementing award-winning application-layer firewalls that monitor, police and restrict access to web servers. We also help customers keep servers and desktops protected and secure by centrally managing application and operating system security updates and patches. Aurora helps protect end point devices by controlling the applications that are allowed to run on them, thus preventing malware from loading on any endpoint device. This is also accomplished by updating all the software regularly on end-point devices.
Our award-winning web security devices provide anti-virus and URL filtering, protecting employees from accessing bad web sites and downloading malicious content. We can filter HTTP and HTTPS traffic, block malware and web-related attacks targeted at our customers and their employees. We provide in-bound and out-bound web traffic protection, helping prevent data leakage on all web protocols. Our partner’s global reputation systems provide advanced, pro-active, zero day protection against known and unknown threats.
Aurora helps our customers secure their end point devices, thus limiting and preventing the vulnerabilities that affect the organization through laptops, desktops and mobile devices like PDAs and SmartPhones. We provide solutions like Av/Spyware, DLP, laptop email/disk encryption, USB/Firewire device encryption, Application WhiteListing, Device Control, Intrusion Prevension and Network Access Control (NAC). All these solutions keep end point devices secure, even when they are not connected to the office network or are used from home or at airports to access the internet or to connect remotely to the office network.
Aurora’s Data Loss Prevention (DLP) protects sensitive privacy data and hard-to-control financial data, source code, formularies, and designs. We remove complexity and manual analysis to help you activate persistent, deep protection quickly and prevent accidental or malicious data loss. We help you discover your information assets, monitor the movement of this data and manage and prevent information access and data leakage respectively. All from one centrally managed console with easy to use and decipher reporting for compliance.
Aurora has solutions to enable PKI applications to operate, generate and store private keys and digital certificates inside a USB-based Token or Smartcard. Our Tokens (Software and/or Hardware Based) can also be used for One-Time Password (OTP) and Single Sign-On (SSO) applications. Our solutions include USB token for data security; a low-cost readerless smart card device that enables strong, two-factor authentication and is easy to deploy. We can provide Secure Access to Your Digital Identity and Information Assets From Anywhere.
Many organization face requirements from internal and external auditors, business partners or regulatory bodies. The security team is required to help provide an analysis of the environment but may not have the breadth of experience to cover all areas of security. Outside assistance is needed to address audit and compliance requirements.
Solution:
An information security audit is an in-depth appraisal of the organization’s adherence to existing policies and industry best practices and identification of areas of weakness that need to be addressed to meet business needs or regulatory and compliance requirements. We will assess the existing weaknesses and develop countermeasures in three area, people, process and technology.
We can analyze your compliance measures against SOX, HIPAA and PCI requirements. We can determine cost effective software, procedures and process compliance measures to adhere to regulatory standards. Through our gap analysis approach, we design a remediation process and identify mitigating controls.
The audit can be broken down into the following areas:
- External – Analyzing the security of the organization’s perimeter from an external perspective.
- Internal – Analyzing the security of the desktops, laptops, servers and storage as well as the existing security processes and procedures from an internal perspective. Areas that can be reviewed include but are not limited to security over intellectual property, vendors, legal and compliance issues, disaster recovery, business continuity, data storage, etc.
- People and Process– Assess vulnerabilities associated with how employees conduct themselves, including contractors, visitors and unauthorized insiders. Review business processes for inherent weaknesses according to industry best practices.
- Physical – Assess the physical controls around information assets for potential vulnerabilities including:
- Environmental disasters
- Deliberate acts of destruction
- Loss of services
- Equipment and system failure
- Serious information security incidents
- Personnel (hiring, firing, transferring/moving) and safety
- Building and property access, monitoring and recording
How the Process Works:
We will be onsite to interview relevant staff, conduct automated testing and review all pertinent documentation. Current practices will be compared to industry best practices and any regulatory requirements that the company must follow. A summary and detailed report will be provided identifying all findings and detailed solutions will be provided to both fix the current problem and change business processes as necessary to avoid the problems from reoccurring. You may choose to have us do a retest using only automated techniques after you have completed the recommended fixes. This will be at a discounted rate.
We provide a programmatic approach for evaluating technical, administrative and management security controls across your environment. The Penetration test is a necessary tactical approach to securing all the “low-hanging” risk in your infrastructure. We will conduct tests against your Internet perimeter and internal systems using real world attacks techniques, both automated and manual.
Our security professionals regularly perform automated and manual penetration tests, using proven techniques, methodologies and tools to detect undesirable risk conditions. External points of attack include Internet routers, firewalls, DNS, the web application, and database servers as well as undocumented hosts that may provide a foothold or deeper pathway into a company’s infrastructure from the web application systems. Attack and Penetration services constitute a highly evolved and structured approach to examining the security functionality of systems. All of our analysis processes are designed to be non-disruptive to the organization in most cases, providing valuable insights into a company’s overall security posture.
An experienced and highly certified Aurora engineer will deploy security solutions and do knowledge transfer. We will train the customers IT staff on best practices, deployment methodologies, policies and integration with existing technology. This includes upgrades and updates. The Aurora engineers can train on solutions offered by PGP, McAfee, Aladdin, Lumension Security and SecurePATH. Training can be expanded to end users and executives as well, on how to use the solutions deployed. Custom documentation may also be created and delivered depending on the project scope and requirements.

